Here is a rough guide of how I have my network laid out. I haven’t really documented it before, so hopefully this covers the major points. I use a number of VLANS in my network to keep the IOT devices from being security threats, and prevent security devices from being able to access the internet (like security cameras).
I will write up a longer guide later on when I have some time, for now the short of it. The hardware is mostly Unifi gear with a Unifi controller running on my Proxmox host. This is the same host I run home assistant on (all virtual machines). The Unifi controller lets me configure my whole network in one pane of glass, its a bit of a pain at times, but for me the convenience has outweighed the higher price and limitations so far.
Hardware
- Unifi USG pro4 (firewall)
- Unifi 24 port 300W POE switch (discontinued beta equipment, but amazing)
- Unifi 16 port 50W POE switch
- Various Unifi 8 port POE powered switches
- Unifi AP U6 Lite (Wi-Fi 6 AP) * 2
VLANs
I setup my VLANs to provide minimum access without removing convenience. This is why my main LAN network has access to all VLANs, while not all VLANs have access back to it. My VLANs:
- IOT secure
- Rules
- ❌ No internet
- ✔ LAN access
- Devices
- WLED
- EspHome
- Rules
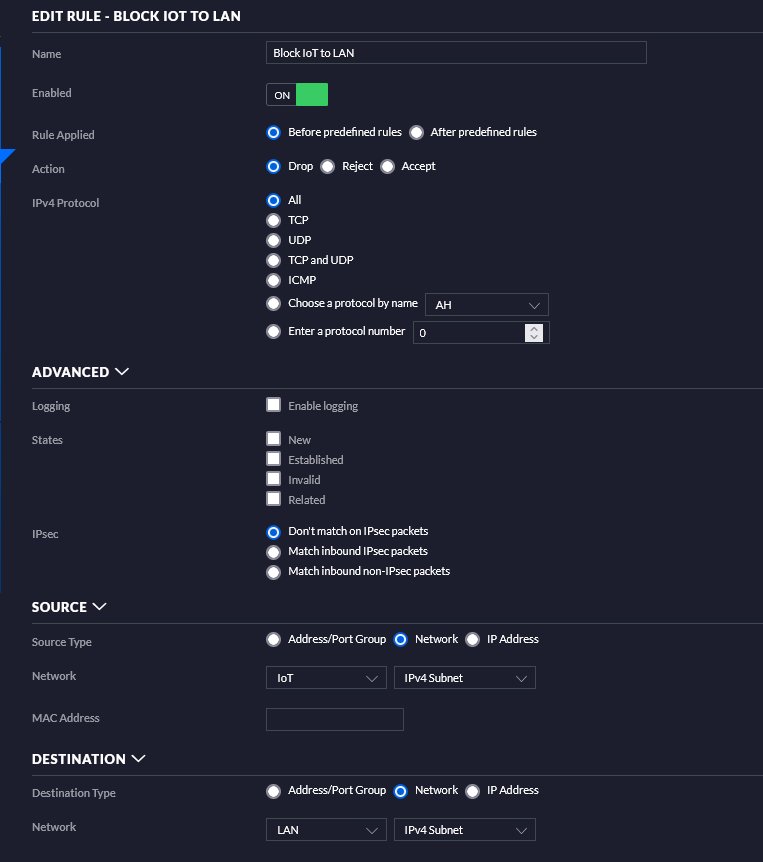
- IOT
- Rules
- ✔ Internet access
- ❌ No LAN access
- Devices
- Ring cameras
- Ring chimes
- Rules
- LAN
- Rules
- ✔ Access to internet
- ✔ Access to all VLANs
- Devices
- Laptops
- Servers
- Desktops
- Rules
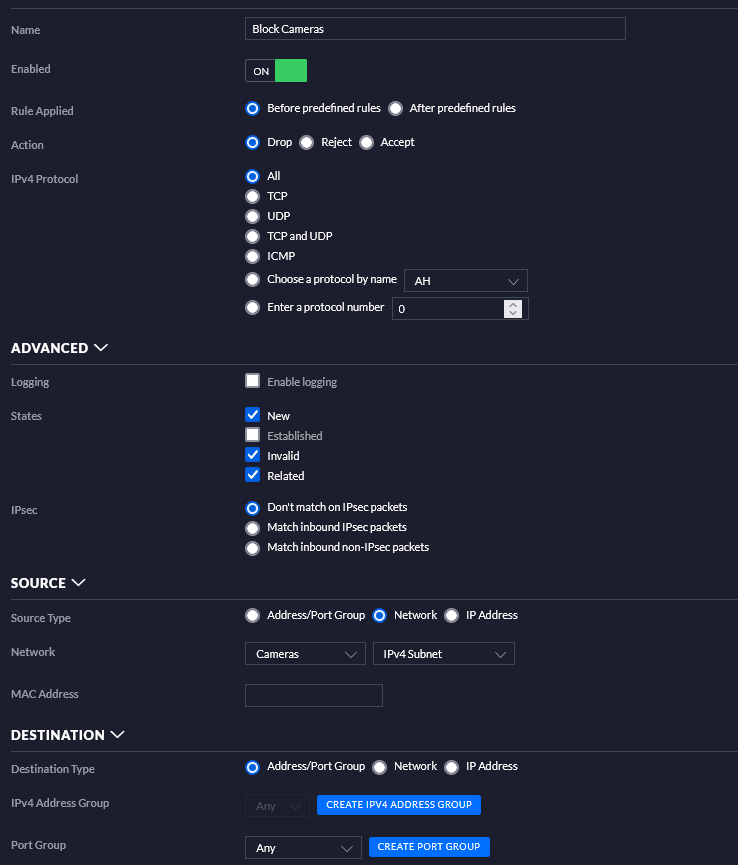
- Cameras
- Rules
- ❌ No LAN access
- ❌ No Internet access
- Devices
- Amcrest cameras
- Unifi cameras
- Rules
I have some others but they aren’t as necessary for the smart home stuff, more on other self hosting. This layout lets me put Ring Devices, ROKUs, and other devices onto a network to prevent them from being an intrusion point, but also allow them to work as expected. The IOT secure network is where my tasmota, esphome, and other wifi devices talk, none of these need internet access, but since some talk through MQTT, they need the ability to talk to my LAN (a future security improvement could be to just allow a single port for MQTT through to the LAN).
I got MDNS working across VLANs recently by using a firewall magic rule: This blog post has more details about it. This helps with getting some IOT devices talking between VLANs (like ESPhome advertising hostnames to home assistant, enabling quicker setup). Below are firewall rules and configurations from these settings.
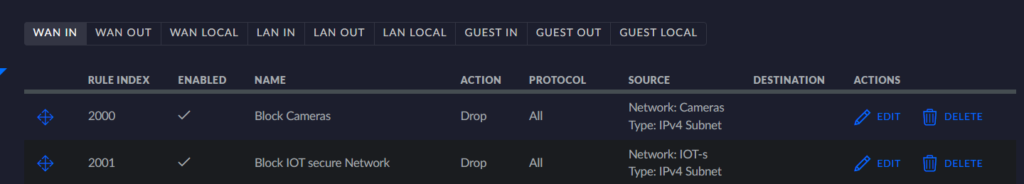
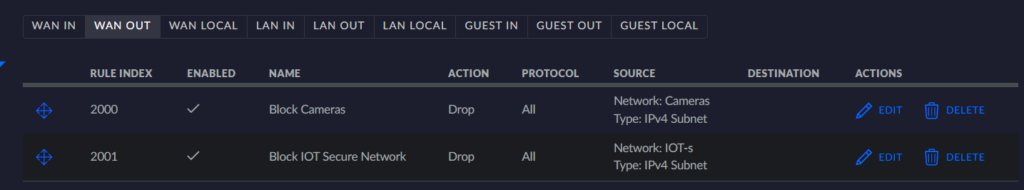
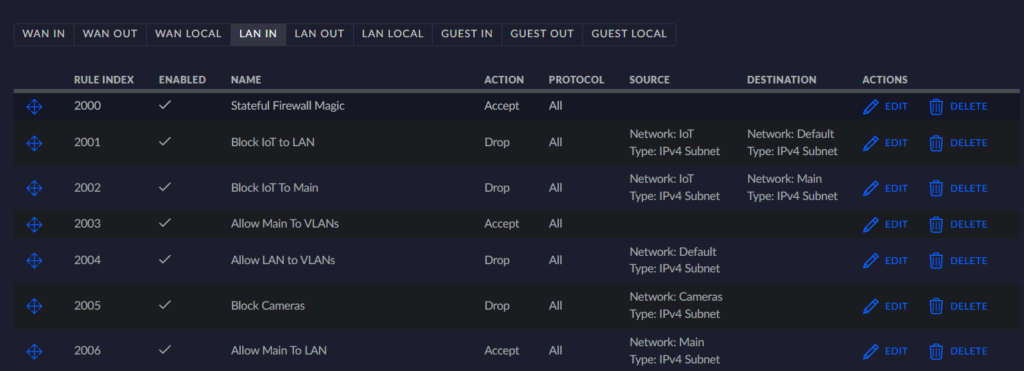
Below is going to be further detail settings from my firewall rules.
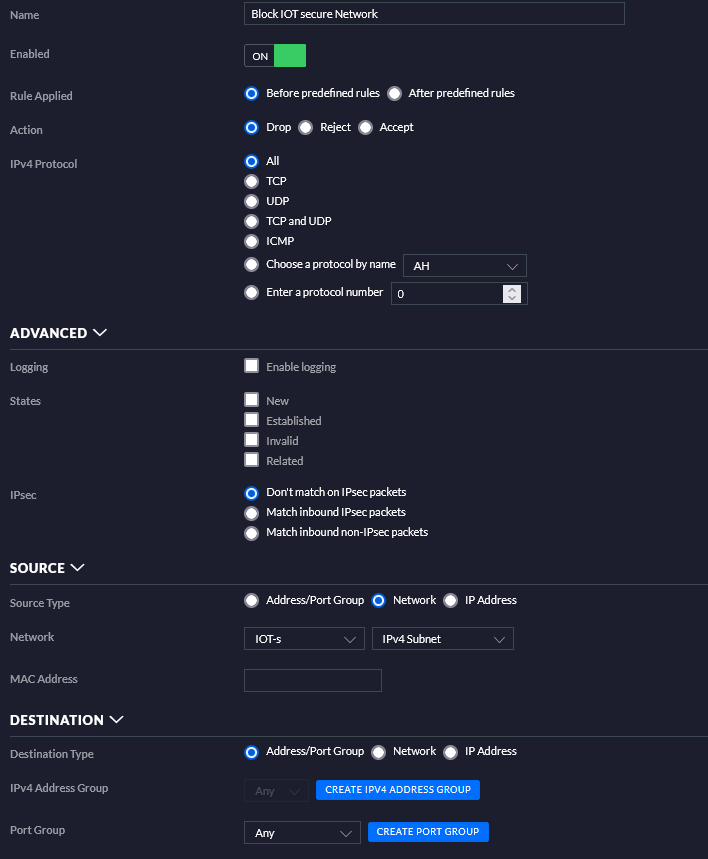
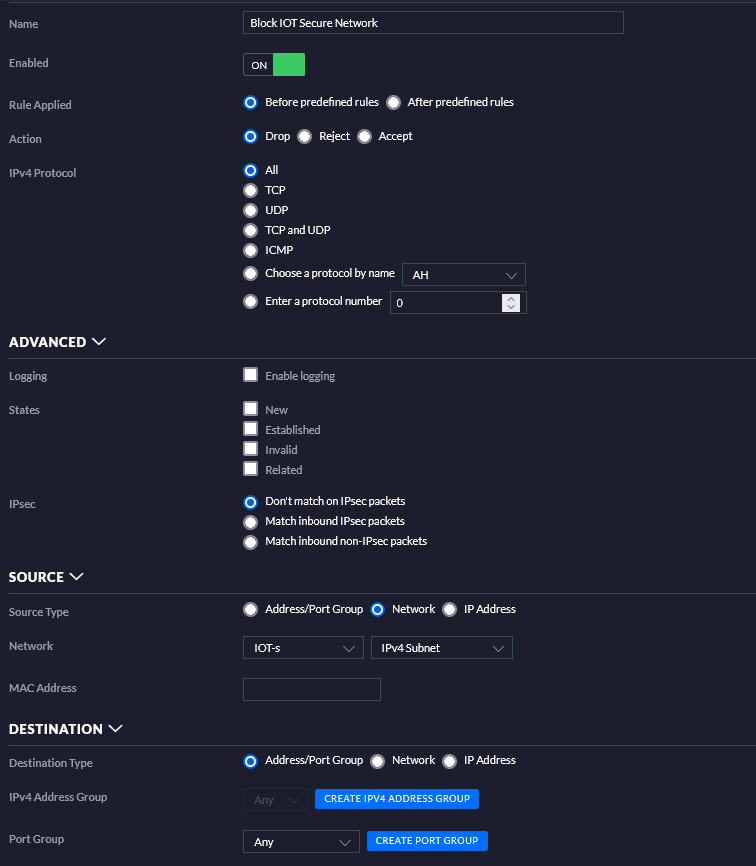
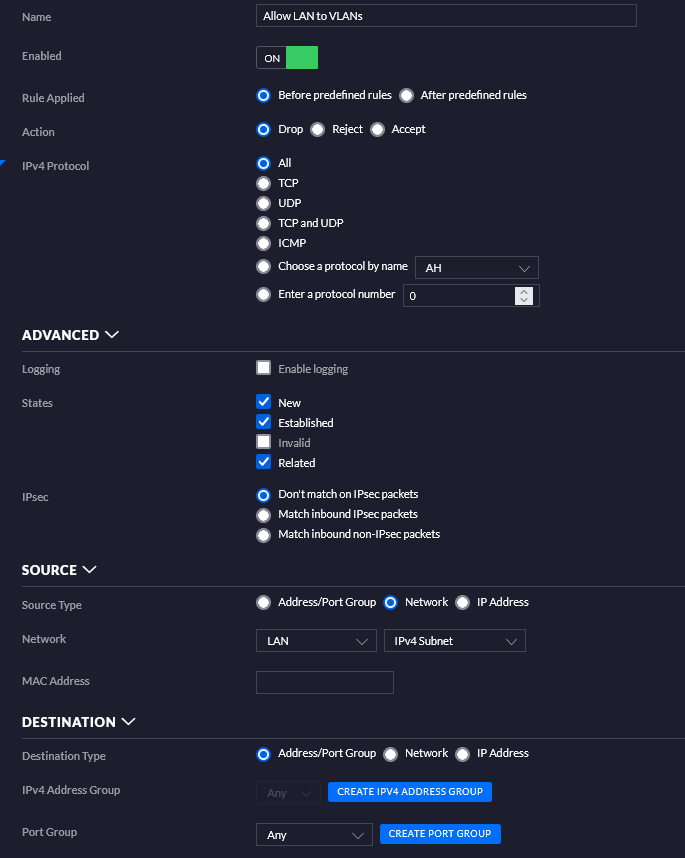
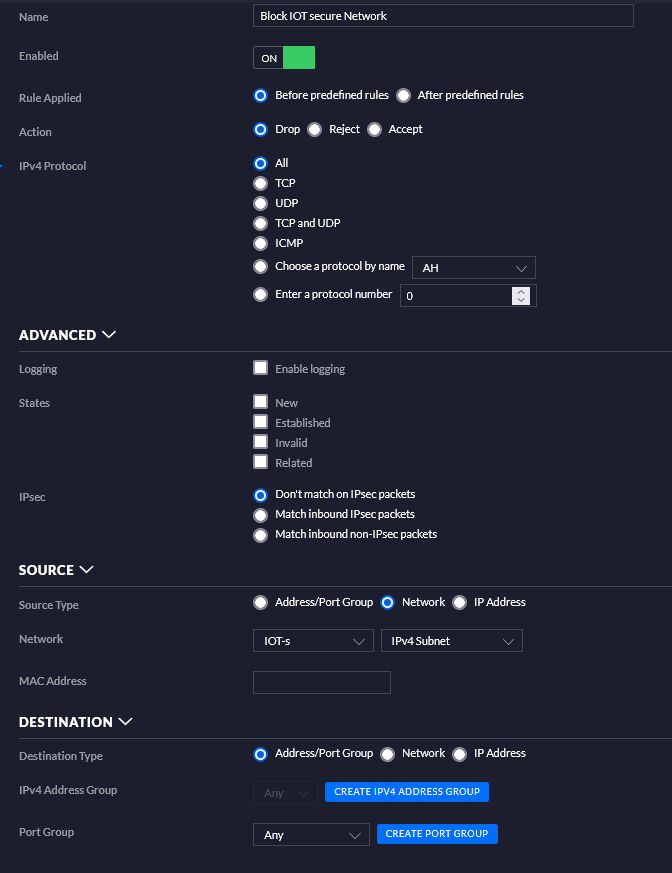
Conclusion
I’ve been running with this VLAN layout and network for a few years now. Its been working out amazingly well, with the main complaint being that I wish I could run with fewer WiFi SSIDs. The Unifi access points end up complaining about too many SSIDs to me and I have to click through some acknowledgements. Maybe I can find a good way to reduce the SSIDs, but still, this being my only complaint, I’m very happy with my network layout and security.
Resources
Acronyms
- AP: Wi-Fi Access Point
- LAN: Local Area Network
- VLAN: Virtual Local Area Network