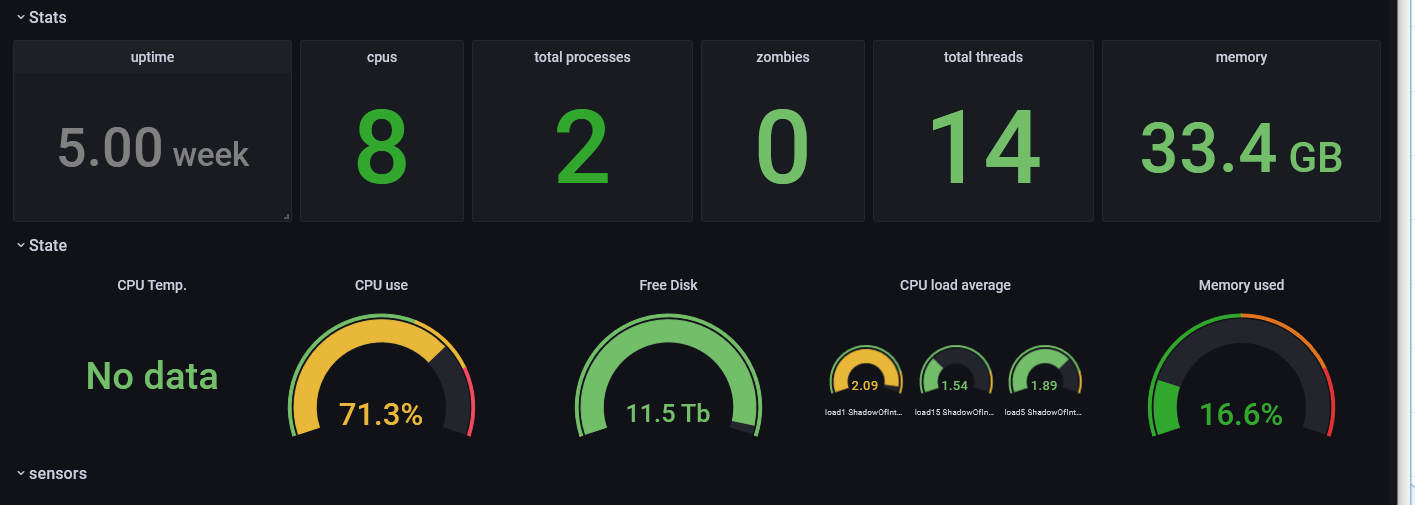
Telegraf was the second service I stepped up to influxdb v2. With this service running on unraid, I’ll be able to start monitoring the system and get my dashboards back up and running. I have some other instances of telegraf that will need to be stepped up that are configured differently, but in this case, I’ll be working on my unraid instance first.
Continue reading “Stepping up Telegraf to Influx V2”Stepping up Grafana to InfluxDB V2
With my InfluxDB V2 container setup, some tokens created, and buckets in place, its time to start stepping up services. The first service to be stepped up will of course be Grafana itself, so that once the other tools are stepped up, I can start using the dashboards again.
Continue reading “Stepping up Grafana to InfluxDB V2”Intro to InfluxDB V2
I have watchtower setup on my Unraid server to handle automatically updating all my docker containers. This is quite convenient, however it does come with some dangers. For instance, my InfluxDB instance recently updated to version 2. This version of influx has a brand new query language, authentication system, and much more. This also breaks all compatibility with my Telegraf, Unifi-Poller, Grafana, and other services. Instead of trying to revert to an older version and refuse the slow change of technology, I decided to just start stepping up services to work with the new version. So I know get to introduce myself to InfluxDB V2 and then to move on to stepping up services to use it.
Continue reading “Intro to InfluxDB V2”Grafana LDAP Authentication
In my adventure to add centralized authentication to a portion of my infrastructure, I decided to add Grafana to my list of apps using LDAP. I have had a Grafana/Influx/Telegraf stack up in my infrastructure for a long time and have no intention of removing it, so its a perfect candidate for this treatment.
While Grafana includes some enterprise features for purchase, we will just be using the free features available. These can be used to setup basic authentication for login, and roles based on LDAP groups. This can provide admin, viewer, and editor capabilities. For my instance, I’ll be focusing on a basic admin user, with all other LDAP logins from my server going to the viewer role.
- Admin
- Administrator user
- Editor
- edit and view dashboards
- Viewer
- view dashboards