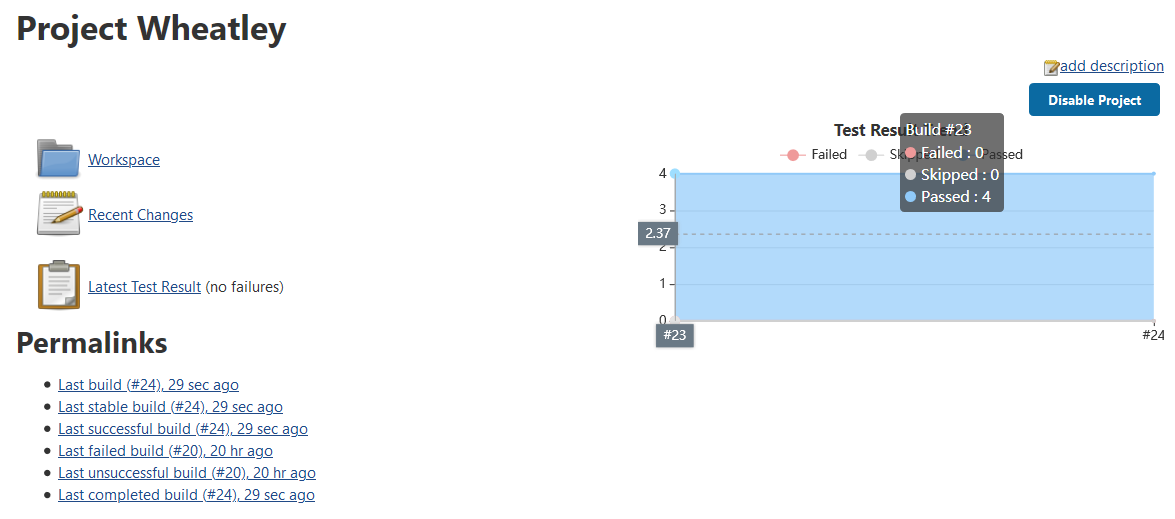
After setting up Jenkins to auto build and deploy my IRC bots, I decided to add the next component of a CI/CD stack, automated testing. This was to use ant to run the tests, and JUnit for the testing framework for the application. I’ll be setting this up in both of my Jenkins projects, I have one that just builds my applications, and a second that builds the docker containers and pushes them to the repository.
My Jenkins setup includes 2 builds for each of my projects:
- Java Build
- Builds the java application
- This is just a general Jenkins project that uses ant to build
- Docker Build
- Builds the docker container, tags it, and pushes it to my local docker repository
- This uses Jenkins pipelines to perform the build, tag, push
The docker build pushes my production code and is used by my docker-swarm to update my locally built containers. This is the important build. The general java build is just me experimenting with Jenkins builds following the non-pipeline route.
Continue reading “Automated Testing in Jenkins”